F0rg3t what you know about creating strong passwords, because the rules have changed. For over a decade we have been trying to make our passwords so random that we end up forgetting if it was a "?" or a "!" in the middle of this jumble of numbers and letters. But that level of obscurity made for a great password. Right? Well, the man who gave us the majority of the tips and tricks we employ when crafting a password now regrets his original advice.
Bill Burr, a retired midlevel manager at the National Institute of Standards and Technology, authored the "NIST Special Publication 800-63. Appendix A" back in 2003. This document advised people to create awkward passwords rife with capital letters, special characters, and numbers — and to change them regularly. This method could result in a password that looks like "P@ssW0rd123!" The problem with this method is that people use the same tendencies when creating their passwords. Hackers can predict these tendencies and use algorithms that target this weakness. To make matters worse, regularly changing passwords does not result in new, secure passwords. If you have ever been asked to change your password, I bet you altered it only slightly to get around having to come up with a new one to remember. Adding another number at the end of the same password, the one you probably use across multiple accounts, doesn't scream security.
An article from The Verge points out a comic from cartoonist Randall Munroe, published back in August 2011. The comic strip poked a hole in this common logic by pointing out how the password “Tr0ub4dor&3” could be cracked in about three days with standard techniques, due to its predictable capitalization, numeric substitutions, and special character use. The password “correct horse battery staple,” written as a single phrase, would take 550 years. (Security experts have confirmed Munroe’s math, according to the WSJ.)
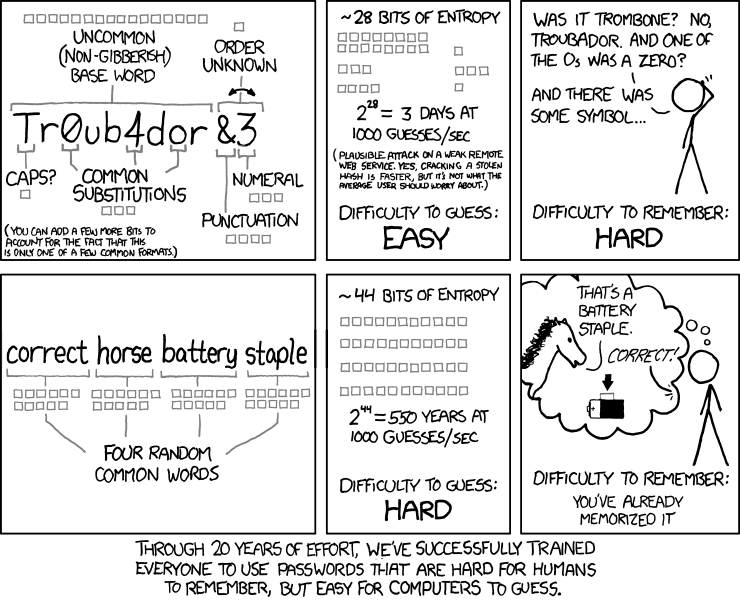
The real kicker is in this last bit of Munroe's comic. We have been trying to make passwords more random, but have actually been making them easier to crack. The new NIST standards, published in June by technical advisor Paul Grassi, did away with much of Burr's advice. The shift in strategy is contained within a section covering authentication and lifecycle in the Digital Identity Guidelines, Special Publication 800-63-3. Grassi did state that Burr's advice held up for over 10 years, and how that is an impressive feat.
The big take away is to use obscure phrases that automated systems can't make sense of. (Two factor authentication is also a great additional layer of security, especially for email and banking sites.) Also, you could always use password managers, which generate cryptographically secure passwords on demand. Yet, you would still need a secure master password, hopefully one that is of the "correct horse battery staple" variety. However, websites need to update their best practices to allow users to adopt this obscure phrase method for their passwords.
-1.png?width=350&height=117&name=iuvo_logo_blue_Transparent%20(1)-1.png)